-
Keyfactor Command is a web-based platform that offers you AI-based tools to manage and handle the identity of the organization and allows you to access the data from any remote location as it is a cloud-based platform.
#Identity Provider #Identity And Access Management #Web Security
-
NOTE: DIGIPASS has been discontinued.DIGIPASS offers two-factor authentication solutions for mobile applications.
#Two Factor Authentication #Identity And Access Management #Authentication
-
Trust strongDM to manage an engineers access to everything
#Governance, Risk And Compliance #Identity And Access Management #Workplace Safety 2 social mentions
-
Simple, unobtrusive authentication for Node.jsPricing:
- Open Source
#Identity Provider #Identity And Access Management #Development 3 social mentions
-
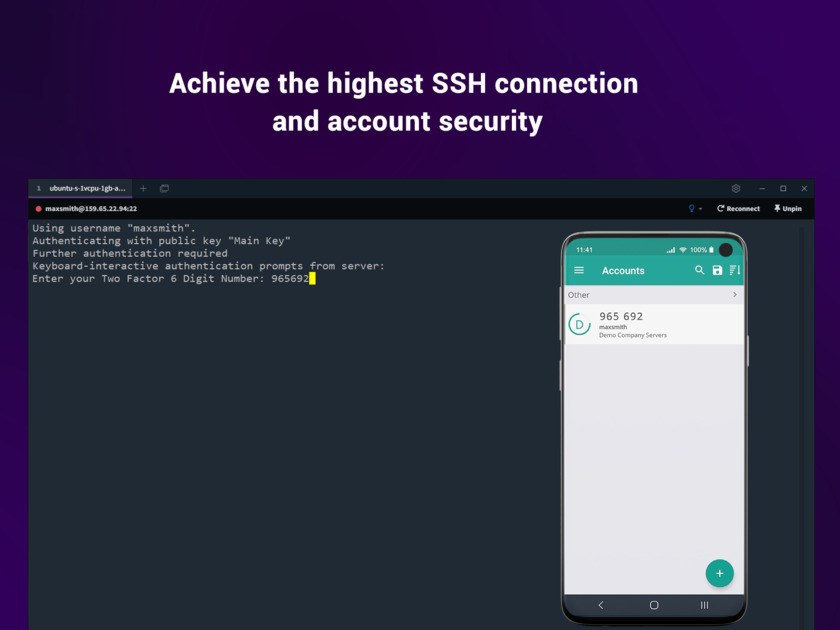
Centralized Linux user and SSH key management softwarePricing:
- Freemium
- Free Trial
- £25.0 / Monthly (Includes 10 Users and 30 Hosts)
#Identity And Access Management #Cyber Security #SSH
-
Userify is a cloud-based SSH key management solution.Pricing:
- Open Source
#Identity And Access Management #Security & Privacy #SSH 6 social mentions
-
Automate endpoint privilege management and mitigate critical vulnerabilities via application control without disrupting users or your IT support team.
#Identity Provider #Identity And Access Management #Cyber Security 1 social mentions
-
Je ziet twee keuzemogelijkheden: Haarlem en Den Bosch. Je gebruikt de optie Haarlem om in te loggen in de Agentdesktop in Haarlem en de optie voor Den Bosch om in te loggen in de Agentdesktop in Den Bosch.
#Identity And Access Management #Tool #Security & Privacy









Product categories
Summary
The top products on this list are Keyfactor Command, DIGIPASS, and strongDM.
All products here are categorized as:
Systems for managing user identities and controlling access to resources.
Tools and clients for securely accessing remote servers via the SSH protocol. SSH stands for 'Secure Shell'.
One of the criteria for ordering this list is the number of mentions that products have on reliable external sources.
You can suggest additional sources through the form here.
Recent Identity And Access Management Posts
10 Best PuTTY Alternatives for SSH Remote Connection
tecmint.com // over 1 year ago
10 Best PuTTY Alternatives To Try in 2024
redswitches.com // over 1 year ago
Looking for MobaXterm Alternative? Here are Some Options to Consider
learnitguide.net // over 2 years ago
Top 12 BEST SSH Clients For Windows – Free PuTTY Alternatives
softwaretestinghelp.com // about 3 years ago
MobaXterm for Mac: Best Alternatives to MobaXterm for Mac
macoszon.com // over 3 years ago
Top 10 Best MobaXterm Alternatives for Windows, macOS & Linux In 2021
techblitz.org // almost 4 years ago
Related categories
Recently added products
Universal SSH Key Manager
Password-Login
sshfs
Turnkey Linux
Ringbot
File in File
Axcient Fusion
One Password
Clerk
TideCloak
If you want to make changes on any of the products, you can go to its page and click on the "Suggest Changes" link.
Alternatively, if you are working on one of these products, it's best to verify it and make the changes directly through
the management page. Thanks!