-
Efficiently derail attacker discovery, lateral movement, privilege escalation, & collection activities early in the attack cycle with Attivo.
#Cyber Security #Security & Privacy #IT And Cybersecurity
-
The most personal application for disc imaging yet.
#CD Image Creator #DVD Image Creator #DVD Image Editor
-
NOTE: Reboot Restore Rx has been discontinued.Reboot Restore Rx (freeware) prevents any and all changes made on your drive(s) making those PC's bulletproof and unbreakable.
#Cloud Storage #Monitoring Tools #Cyber Security 5 social mentions
-
Keyfactor Command is a web-based platform that offers you AI-based tools to manage and handle the identity of the organization and allows you to access the data from any remote location as it is a cloud-based platform.
#Identity Provider #Identity And Access Management #Web Security
-
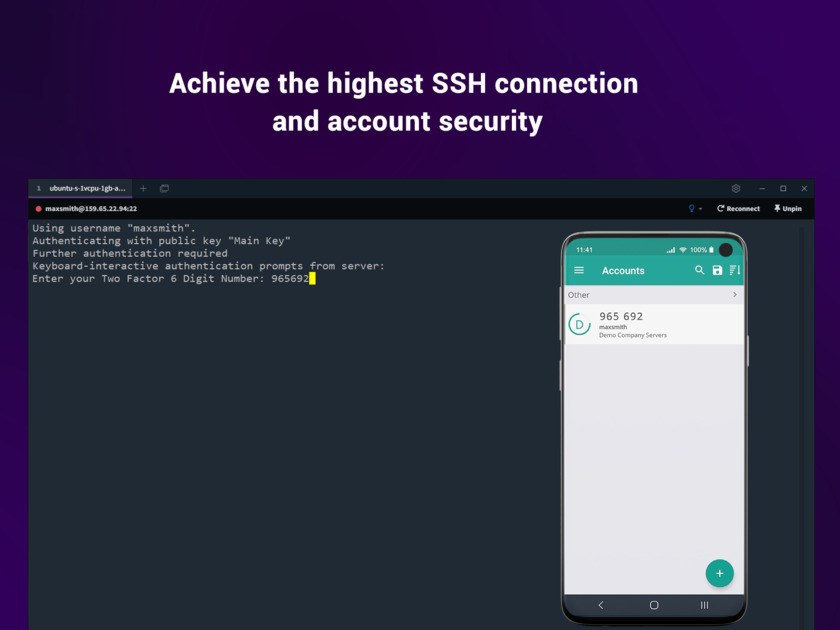
Centralized Linux user and SSH key management softwarePricing:
- Freemium
- Free Trial
- £25.0 / Monthly (Includes 10 Users and 30 Hosts)
#Identity And Access Management #Cyber Security #SSH
-
Automate endpoint privilege management and mitigate critical vulnerabilities via application control without disrupting users or your IT support team.
#Identity Provider #Identity And Access Management #Cyber Security 1 social mentions
-
Sophos develops products for communication endpoint, encryption, network security, email security and mobile security.
#Testing #Monitoring Tools #Localhost Tools 4 social mentions








Product categories
Summary
The top products on this list are Attivo Networks, DAEMON Tools, and Tiger.
All products here are categorized as:
Software and tools focused on protecting computer systems, networks, and data from digital attacks, unauthorized access, and other online threats.
Tools and clients for securely accessing remote servers via the SSH protocol. SSH stands for 'Secure Shell'.
One of the criteria for ordering this list is the number of mentions that products have on reliable external sources.
You can suggest additional sources through the form here.
Recent Cyber Security Posts
10 Best PuTTY Alternatives for SSH Remote Connection
tecmint.com // over 1 year ago
10 Best PuTTY Alternatives To Try in 2024
redswitches.com // over 1 year ago
Looking for MobaXterm Alternative? Here are Some Options to Consider
learnitguide.net // over 2 years ago
Top 12 BEST SSH Clients For Windows – Free PuTTY Alternatives
softwaretestinghelp.com // about 3 years ago
MobaXterm for Mac: Best Alternatives to MobaXterm for Mac
macoszon.com // over 3 years ago
Top 10 Best MobaXterm Alternatives for Windows, macOS & Linux In 2021
techblitz.org // almost 4 years ago
Related categories
🔒 Security & Privacy
🔑 Identity And Access Management
📟 Monitoring Tools
📂 IT And Cybersecurity
🔐 Identity Provider
Recently added products
APN on-off Widget
Humio
WPS Hide Login
WP Hide & Security Enhancer
MalCare Security Service
6Scan
iThemes Security
Defender
w3af
NinjaFirewall (WP Edition)
If you want to make changes on any of the products, you can go to its page and click on the "Suggest Changes" link.
Alternatively, if you are working on one of these products, it's best to verify it and make the changes directly through
the management page. Thanks!