-
PingDoctor is software that is considered to be the most powerful and easiest to use network route analyzer.
#Log Management #Security #Monitoring Tools
-
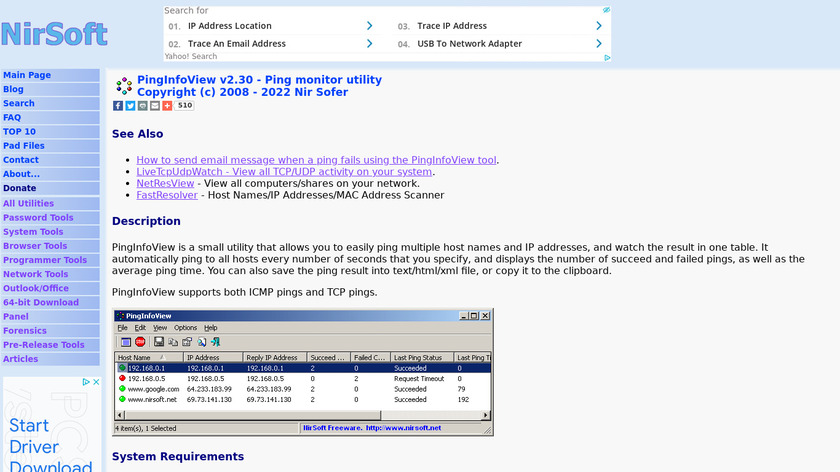
PingInfoView is a small utility that allows you to easily ping multiple host names and IP addresses, and watch the result in one table.
#Log Management #Security #Monitoring Tools
-
sshuttle: where transparent proxy meets VPN meets sshPricing:
- Open Source
#Security #VPN #Cloud VPN 28 social mentions
-
NOTE: UltraSurf has been discontinued.UltraSurf is a free (but not open source) software utility that lets computer users bypass both government firewalls and censorship, through the use of HTTP proxy servers. Read more about UltraSurf.
#Security #VPN #Security & Privacy
-
i2pd (I2P Daemon) is a full-featured C++ implementation of I2P clientPricing:
- Open Source
#Security #VPN #Security & Privacy 10 social mentions
-
PingPlotter is a troubleshooting tool that helps IT professionals and neophytes identify, diagnose, and resolve network issues.
#Monitoring Tools #OS & Utilities #File Transfer 2 social mentions
-
Over 60 great tools to help network engineers troubleshoot issues before users are affected. Download a 14-day trial and explore all the tools for free!
#Security Monitoring #Security #Network Security
-
Keyfactor Command is a web-based platform that offers you AI-based tools to manage and handle the identity of the organization and allows you to access the data from any remote location as it is a cloud-based platform.
#Identity Provider #Identity And Access Management #Web Security








Product categories
Summary
The top products on this list are PingDoctor, PingInfoView, and sshuttle.
All products here are categorized as:
Software focused on protecting systems, networks, and data from cyber threats.
Tools and clients for securely accessing remote servers via the SSH protocol. SSH stands for 'Secure Shell'.
One of the criteria for ordering this list is the number of mentions that products have on reliable external sources.
You can suggest additional sources through the form here.
Recent Security Posts
10 Best PuTTY Alternatives for SSH Remote Connection
tecmint.com // over 1 year ago
10 Best PuTTY Alternatives To Try in 2024
redswitches.com // over 1 year ago
Looking for MobaXterm Alternative? Here are Some Options to Consider
learnitguide.net // over 2 years ago
Top 12 BEST SSH Clients For Windows – Free PuTTY Alternatives
softwaretestinghelp.com // about 3 years ago
MobaXterm for Mac: Best Alternatives to MobaXterm for Mac
macoszon.com // over 3 years ago
Top 10 Best MobaXterm Alternatives for Windows, macOS & Linux In 2021
techblitz.org // almost 4 years ago
Related categories
Recently added products
Veriff Station
Thinkst Canary
Nest Mobile
WinDump
OzCode
Resolve.io
Netsleuth IP
IPCalc Android
SecureWorks
Aviatrix
If you want to make changes on any of the products, you can go to its page and click on the "Suggest Changes" link.
Alternatively, if you are working on one of these products, it's best to verify it and make the changes directly through
the management page. Thanks!