-
NSFOCUS provides comprehensive, end-to-end protection from the debilitating effects of DDoS attacks.
#Bug Bounty As A Service #Network Security #Cyber Security
-
EventSentry is a real-time log management, network and server health monitoring solution.
#Identity Provider #Identity And Access Management #Cyber Security
-
Security for the Heart of the EnterprisePricing:
- Open Source
#Password Management #Password Managers #Security
-
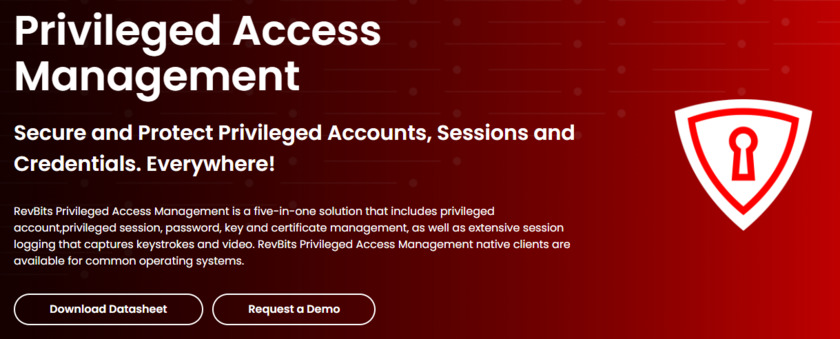
Revbits privileged access management (PAM) provides a comprehensive solution that includes privileged account, password, key and certificate management. Know more about the RevBits (PAM) solutions.Pricing:
- Free Trial
#Password Management #Security Information And Event Management (SIEM) #Cyber Security
-
miniOrange's PAM solution features Password Vault and Rotation, Session Monitor & Control, PASM, PEDM, JIT Privileged Access, Agentless PAM, and Endpoint Privilege Management for comprehensive security and efficient access control.Pricing:
- Paid
- Free Trial
#Identity And Access Management #Cyber Security #Remote Management
-
BeyondTrust’s Privileged Access Management platform protects your organization from unwanted remote access, stolen credentials, & misused privileges
#Password Management #Cyber Security #Security & Privacy
-
Protect your data with identity theft protection & credit monitoring that includes 3-bureau credit reporting, dark web scans, fraud alerts, & more.
#Identity And Access Management #Cyber Security #Remote Management 1 social mentions
-
Secure Active Directory user logins with two factor authentication, single sign-on, contextual access controls and real-time monitoring and reporting.Pricing:
- Paid
- Free Trial
- $2.5 / Monthly (per user)
#Two Factor Authentication #Identity And Access Management #Multi-factor Authentication 1 social mentions
-
Alert Logic lets you collect, aggregate, and search event log files from cloud, server, application, security, container, and network assets across your environments and cloud.
#Log Management #Event And Log Data Analysis #Monitoring Tools









Product categories
Summary
The top products on this list are NSFOCUS, EventSentry, and Cyberark.
All products here are categorized as:
Software and tools focused on protecting computer systems, networks, and data from digital attacks, unauthorized access, and other online threats.
Privileged Access Management.
One of the criteria for ordering this list is the number of mentions that products have on reliable external sources.
You can suggest additional sources through the form here.
Related categories
🔑 Identity And Access Management
🔐 Password Management
🔒 Security & Privacy
📂 Remote Management
🌐 Web Security
Recently added products
APN on-off Widget
Humio
WPS Hide Login
WP Hide & Security Enhancer
MalCare Security Service
6Scan
iThemes Security
Defender
w3af
NinjaFirewall (WP Edition)
If you want to make changes on any of the products, you can go to its page and click on the "Suggest Changes" link.
Alternatively, if you are working on one of these products, it's best to verify it and make the changes directly through
the management page. Thanks!