-
NOTE: GFI EventsManager has been discontinued.GFI EventsManager offers solutions to manage event log data for system reliability, security, availability and compliance.
#Log Management #GDPR Compliance #Security Information And Event Management (SIEM)
-
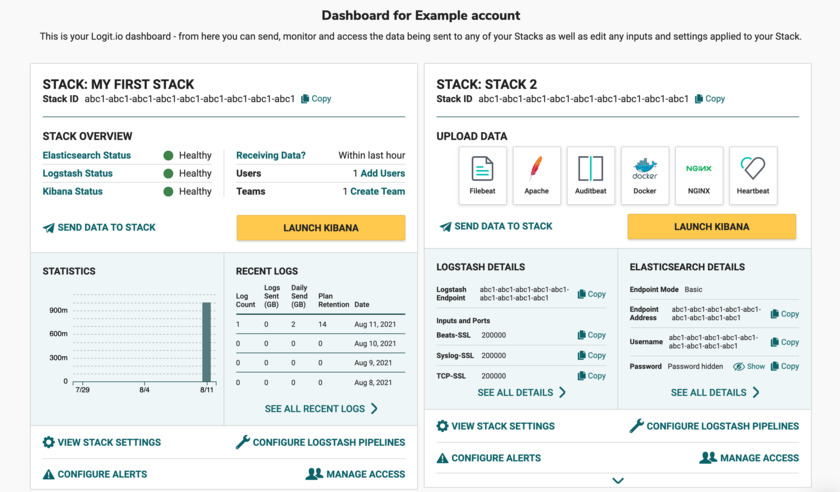
Logit.io provides complete observability of logs, metrics and traces. The platform also offers alerting & monitoring, as well as Prometheus, OpenSearch & Grafana. Ingest any type of data to see real-time insights about your applications and servicesPricing:
- Open Source
- Paid
- Free Trial
- $0.74 (per GB per day)
#APM #Log Management #Security Information And Event Management (SIEM)
-
NOTE: quadrantsec.com Sagan has been discontinued.Get a high performance, real-time log analysis & correlation engine
#Security Information And Event Management (SIEM) #Event And Log Data Analysis #Monitoring Tools
-
The world's most popular cloud log management service delivers application intelligence. No Software. No Downloads. No Sweat. Free Trial!
#Log Management #Performance Monitoring #Monitoring Tools 1 social mentions
-
McAfee Enterprise Log Manager automates log management and analysis for all log types and integrates with McAfee Enterprise Security Manager for analysis and incident management.
#Log Management #Security Information And Event Management (SIEM) #Event And Log Data Analysis
-
EventSentry is a real-time log management, network and server health monitoring solution.
#Identity Provider #Identity And Access Management #Cyber Security
-
NOTE: logz.io ELK Stack has been discontinued.The ELK Stack combines three open source solutions:Elasticsearch, Logstash, and Kibana.It is used by well known organizations like Microsoft and Facebook to monitor log data.There is also a Bitnami ELK Stack For Windows / Linux / MacOS.
#Log Management #Testing #Performance Monitoring 4 social mentions
-
LOGalyze - Search, find, analyze - Open Source Log management, SIEM, Log analysis tool
#Log Management #Security Information And Event Management (SIEM) #Monitoring Tools
-
Qbox is fully-managed, Hosted Elasticsearch for turn-key ELK Stack applications. Features CPU/RAM control, custom pricing, and free 24/7 production support.
#Monitoring Tools #Search Engine #Custom Search









Product categories
Summary
The top products on this list are GFI EventsManager, logit.io, and quadrantsec.com Sagan.
All products here are categorized as:
Tools for managing security events and information.
Event And Log Data Analysis.
One of the criteria for ordering this list is the number of mentions that products have on reliable external sources.
You can suggest additional sources through the form here.
Recent Security Information And Event Management (SIEM) Posts
Related categories
📟 Monitoring Tools
📈 Log Management
📈 Machine Data Analytics
📊 Performance Monitoring
🔒 Security & Privacy
Recently added products
Global Public Safety
amon
Chats.Directory
Who's Responding
ZyLAB Investigation
synk.to
Punch Clock
AIDE
CA Top Secret
Shell Control Box
If you want to make changes on any of the products, you can go to its page and click on the "Suggest Changes" link.
Alternatively, if you are working on one of these products, it's best to verify it and make the changes directly through
the management page. Thanks!