Hudson Rock
Hudson Rock’s products — Cavalier & Bayonet — are powered by our continuously augmented cybercrime database, composed of millions of machines compromised in global malware spreading campaigns.
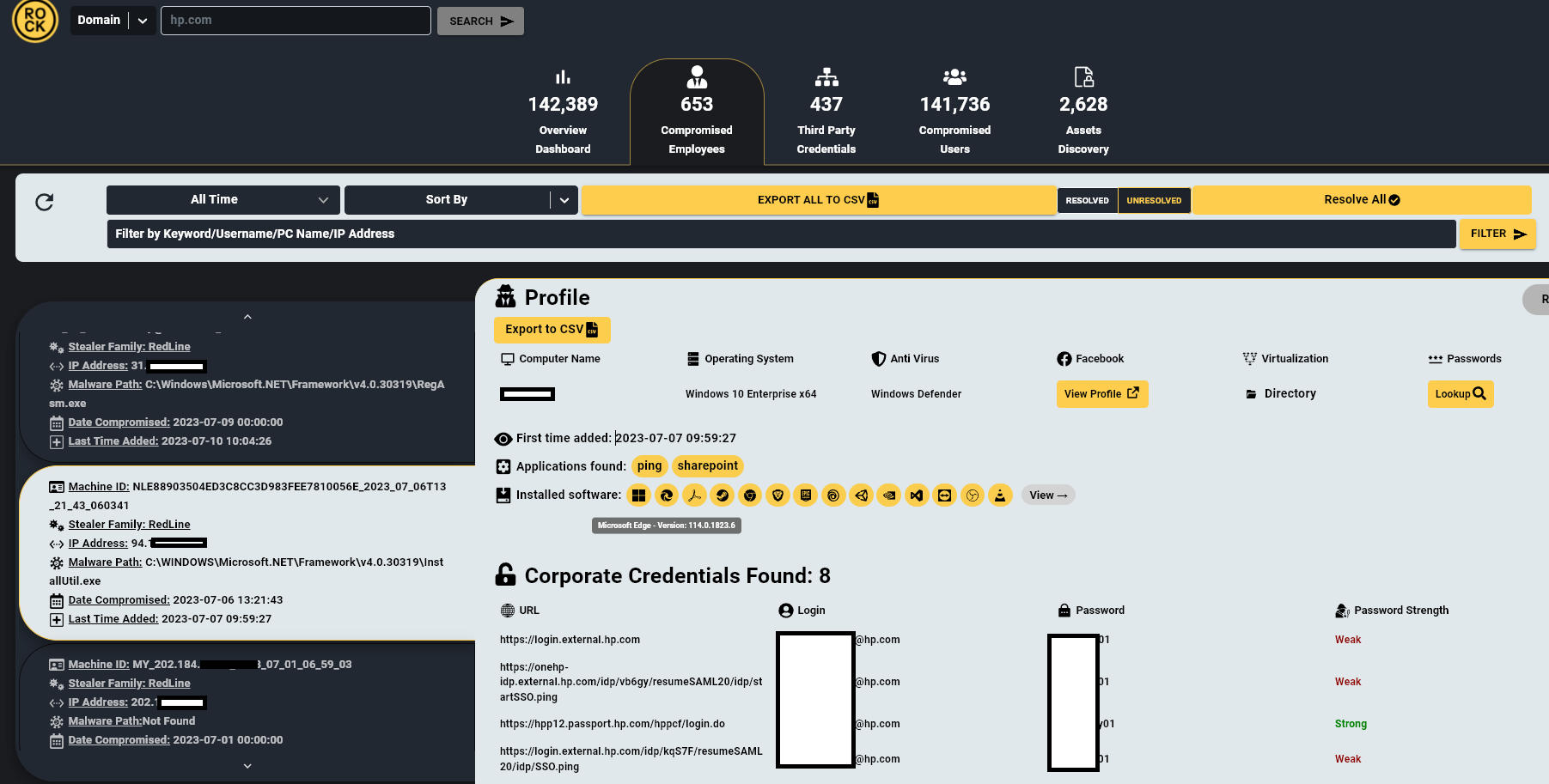
Cavalier™ — For Threat Intelligence Professionals.
Are you a security professional charged with bolstering platform integrity and defending against Account Take Over (ATO), Ransomware Attacks & Corporate Espionage?
With Cavalier™ you will be immediately notified about Compromised Credentials belonging to your Employees, Customers, Users & Vendors.
Cavalier™ Includes: - Compromised Employees - Compromised Customers & Users - Compromised Supply Chain - Compromised Android Users - Compromised Leaked Database - Compromised CXO’s & Family Members
Bayonet™ — For Cybersecurity Sales Teams & MSSPs
Are you a sales professional selling products and services in the cybersecurity space looking for more leads and prospects?
With Bayonet™ you get access to hundreds of thousands of compromised companies around the world with active vulnerabilities that you can convert into customers.
Bayonet™ Includes: - Search for Prospects by Name - Search by Geography - Search by Industry - Search for Prospects by Login Infrastructure - Granular Supply Chain Risk Assessments - Compromised Credentials
- Browser
- Windows
- Linux