✓
Remote.it
Connectivity as Code. Unlock the power of networking without hardware. Instant, secure, and code-bassed networking solutions for seamless network connectivity across all devices and services.
Revolutionizing Network Connectivity Replaces manual network configuration with Zero Trust
Remote.It revolutionizes network connectivity by offering Zero Trust Network Connectivity as a Service. It creates private internet networks, visible only to you, thus enhancing privacy and security.
Remote.It replaces VPNs and manual network management with a Zero Trust approach, providing seamless connectivity, efficient network management, and elevated security. Its unique technology ensures connections without public IP addresses, making it ideal for CGNAT networks such as Mobile 5G and Starlink. It automates IP address planning, resolves subnet collisions, and simplifies complex network tasks. Additionally, it prioritizes enhanced security by granting access to specific services, not subnets, thus protecting private resources from bots and malicious actors.
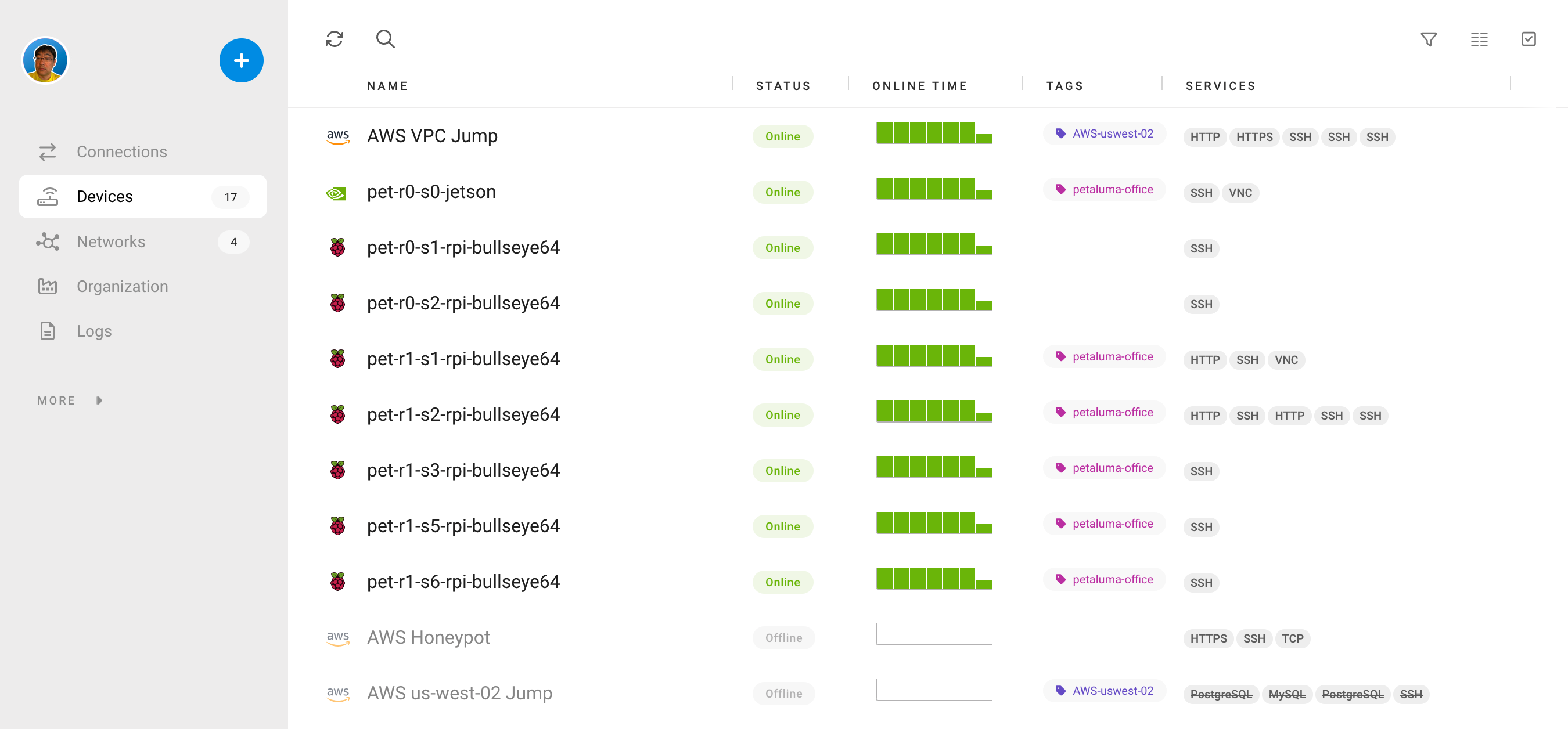
Remote.It exhibits resilience to network changes or moving devices, automatically reconnecting connections. It tackles network management challenges like IP address overlaps and subnet collisions. It minimizes external attack surfaces, negating the need for IP address or port forwarding. This makes it a superior choice where traditional VPNs may fail, particularly in multi-NAT or CGNAT environments.
Remote.It's versatility is showcased across IoT & OT, Devices, Developers, and Docker. It enables remote access on any network, allows pre-deployment connectivity integration into OEM and embedded products, and offers developers hassle-free access to multiple private networks. It simplifies access to services within container networks for Docker users, eliminating the need for routing tables.
Remote.It is committed to securely connecting everything, allowing users to build private networks within the internet. It is preferred for developers and DevOps users seeking dependable, secure remote connectivity and VPN alternatives.
- Freemium
- $25.0 / Monthly (Business plan, per user per month)
- Official Pricing
- Windows
- MacOS
- iOS
- Android
- Linux
- AWS
- Azure
- Arm Virtual Hardware