-
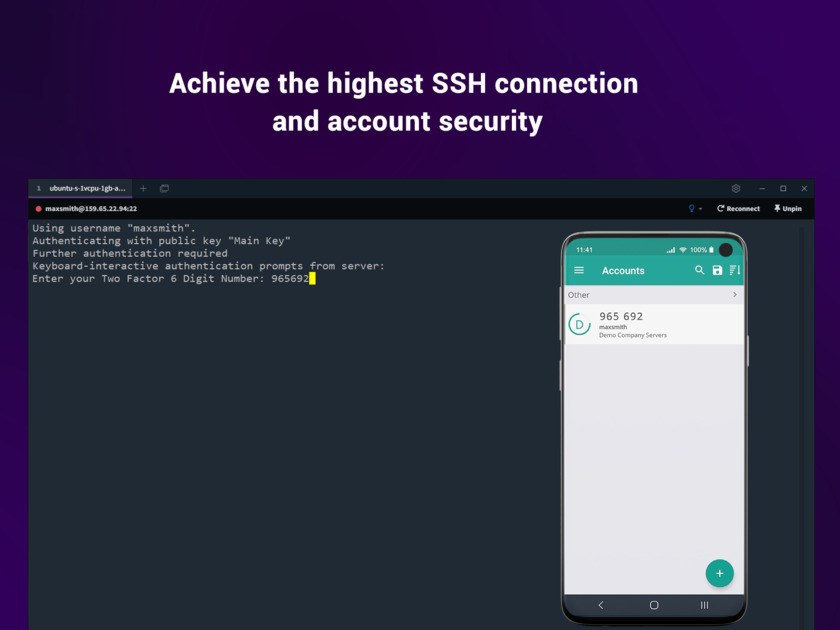
Userify is a cloud-based SSH key management solution.Pricing:
- Open Source
#Identity And Access Management #Security & Privacy #IT And Cybersecurity 6 social mentions
-
Enterprise-grade access controls for your secure shell infrastructure.
#Identity And Access Management #SSH #Security & Privacy
-
The world's most famous hacker Kevin Mitnick leads an elite white-hat team to provide the planet?s best penetration testing, security assessments and training.
#Monitoring Tools #Cloud Storage #ERP
-
Keyfactor Command is a web-based platform that offers you AI-based tools to manage and handle the identity of the organization and allows you to access the data from any remote location as it is a cloud-based platform.
#Security & Privacy #Identity And Access Management #Web Security
-
Centralized Linux user and SSH key management softwarePricing:
- Freemium
- Free Trial
- £25.0 / Monthly (Includes 10 Users and 30 Hosts)
#IT And Cybersecurity #Identity And Access Management #Cyber Security
-
Appviewx Cert is a next-generation certificate management suite that simplifies X.509 certificates, SSH keys, and crypto technologies across user and host endpoints.
#Network & Admin #Domain Name Registrar #Domain Names
-
Automate endpoint privilege management and mitigate critical vulnerabilities via application control without disrupting users or your IT support team.
#Identity And Access Management #Identity Provider #Security & Privacy 1 social mentions







Product categories
Summary
The top products on this list are Userify, Universal SSH Key Manager, and Mitnick Security.
All products here are categorized as:
Tools and clients for securely accessing remote servers via the SSH protocol. SSH stands for 'Secure Shell'.
IT And Cybersecurity.
One of the criteria for ordering this list is the number of mentions that products have on reliable external sources.
You can suggest additional sources through the form here.
Related categories
🔑 Identity And Access Management
🔒 Security & Privacy
🔐 Identity Provider
🔌 Network & Admin
📟 Monitoring Tools
If you want to make changes on any of the products, you can go to its page and click on the "Suggest Changes" link.
Alternatively, if you are working on one of these products, it's best to verify it and make the changes directly through
the management page. Thanks!