Table of contents
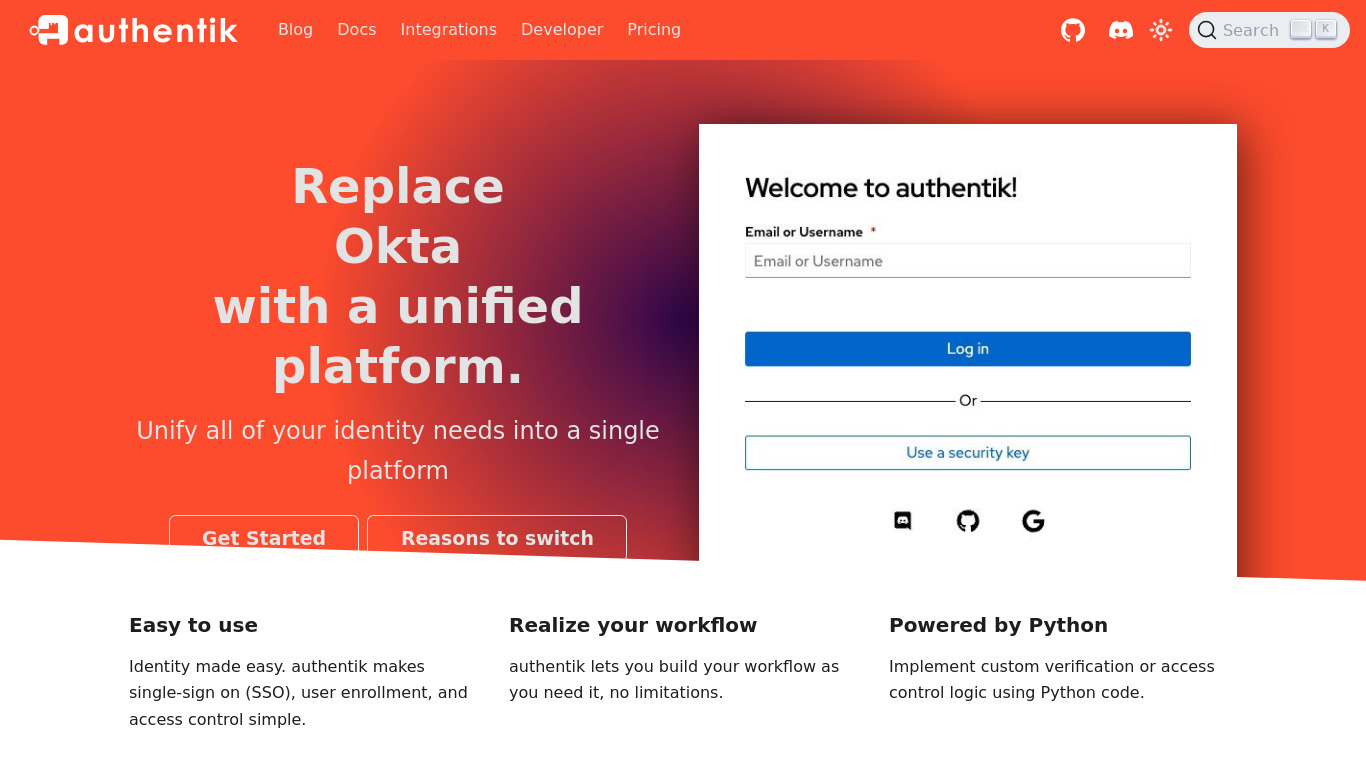
authentik
authentik is an open-source identity provider focused on flexibility and versatility.
As authentik is an open source project, you can find more
open source alternatives and stats
on LibHunt.
Pricing:
- Open Source