-
Nessus Professional is a security platform designed for businesses who want to protect the security of themselves, their clients, and their customers.
#Web Application Security #Security #Monitoring Tools
-
Nessus identifies the vulnerabilities, policy-violating configurations, and malware that attackers could use to penetrate your network.
#Monitoring Tools #Vulnerability Scanner #Cyber Security
-
Hackers know your weak points. Do you?
#Vulnerability Scanner #Cyber Security #Penetration Testing
-
Zeguro provides complete cybersecurity risk assessment, mitigation, and insurance, allowing you to easily manage your cyber risk.
#Cyber Security #IT And Cybersecurity #Cyber Intelligence Platform
-
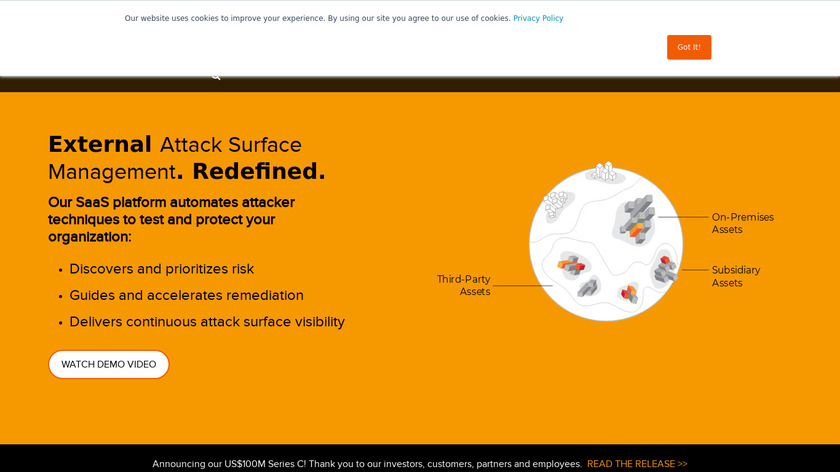
NOTE: CyCognito has been discontinued.Proactive attack surface protection that prevents breaches. See your risks as attackers do. Know what to fix first. Remediate faster. Spend Less
#Security #Vulnerability Scanner #Cyber Security
-
Control Your Security. Keep Control of Your Time.
#Security #Vulnerability Scanner #Cyber Security
-
Detect, prevent, and respond to attacks with next-generation endpoint protection.
#AI #Antivirus #Cyber Security
-
We stop breaches by emulating attackers.
#Web Application Security #Security #Cyber Security









Product categories
Summary
The top products on this list are Nessus, Nessus Vulnerability Scanner, and Red Sentry.
All products here are categorized as:
Vulnerability Scanner.
IT And Cybersecurity.
One of the criteria for ordering this list is the number of mentions that products have on reliable external sources.
You can suggest additional sources through the form here.
Related categories
Recently added products
runZero
OneUp Networks
Bug Bounty Hunt
MIA APP
Ai1 Security Website Scanner
BeyondTrust
HomeDock OS
Spyse
CollectCore
mimikatz
If you want to make changes on any of the products, you can go to its page and click on the "Suggest Changes" link.
Alternatively, if you are working on one of these products, it's best to verify it and make the changes directly through
the management page. Thanks!