-
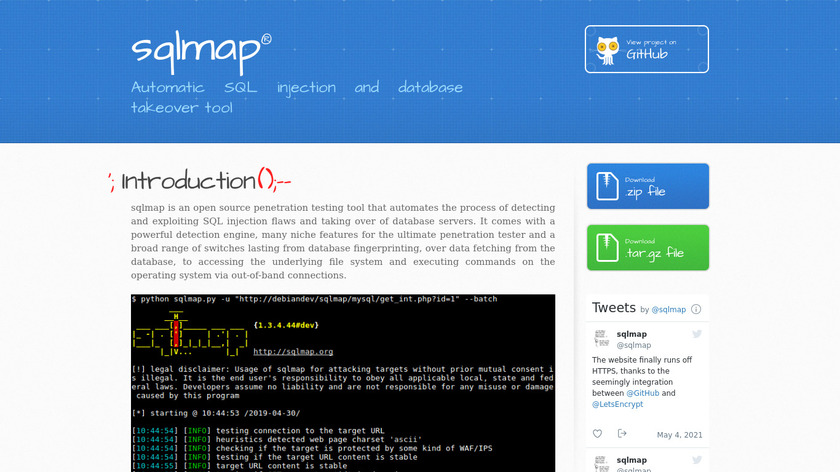
sqlmap is an open source penetration testing tool that automates the process of detecting and...Pricing:
- Open Source
In the first scenario, the exposed application is running on a Kubernetes cluster and the attacker wants to access the data without authorization. The first thing the attacker could check is if the application can be exploited through normal pentesting techniques, for example, with SQLmap the attacker can try to gain access to the data.
#Web Application Security #Security #Vulnerability Scanner 17 social mentions
-
An open-source systems monitoring and alerting toolkit.Pricing:
- Open Source
Prometheus is the de facto monitoring standard in Kubernetes. All the Kubernetes components of the control plane generate Prometheus metrics out of the box, and many Kubernetes distributions come with Prometheus installed by default including a series of standard exporters, generally:.
#Monitoring Tools #Performance Monitoring #Log Management 225 social mentions
-
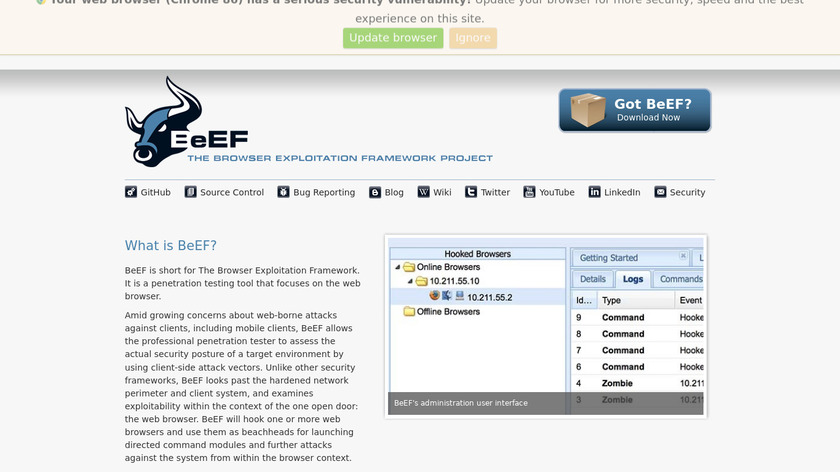
BeEF is browser exploitation framework that is a penetration testing tool that focuses on the web browser.Pricing:
- Open Source
Third-party registry: In this case, one of the methods could be social engineering, using tools like BeeF to create a specific phishing or fake page to get the login credentials and change the image to a new one with a known and exploitable vulnerability and wait for the deployment. One more thing is this is not magic or 100% successful. If the company scans the images in the deployment, it could be detected!
#Security #Web Application Security #Testing 13 social mentions



Discuss: How attackers use exposed Prometheus server to exploit Kubernetes clusters
Related Posts
10 Best Grafana Alternatives [2023 Comparison]
sematext.com // 4 months ago
Top 10 Grafana Alternatives in 2024
middleware.io // 3 months ago
5 Best Password Managers for Teams (2024)
teampassword.com // 10 months ago
10 Best Free Firewall Software for Windows in 2024
geeksforgeeks.org // 6 months ago
Best Free Firewalls for Windows, Mac & Android in 2024
wizcase.com // 3 months ago
Best firewall software of 2024
techradar.com // 2 months ago