IronWASP
Learn, download and use the most flexible and powerful web application security testing framework. subtitle
IronWASP Alternatives
The best IronWASP alternatives based on verified products, community votes, reviews and other factors.
-
/horangi-alternatives
Horangi is a leading cyber-security solution that provides instant response and threat detection for companies who lack the time and expertise to monitor their system.
-
/practiceprotect-alternatives
Network security & identity management
-
Try for free
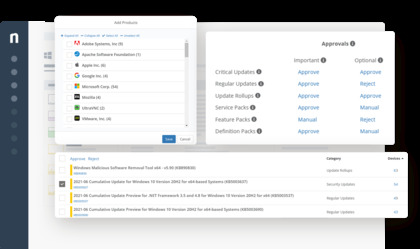
NinjaOne (Formerly NinjaRMM) provides remote monitoring and management software that combines powerful functionality with a fast, modern UI. Easily remediate IT issues, automate common tasks, and support end-users with powerful IT management tools.
-
/acunetix-alternatives
Audit your website security and web applications for SQL injection, Cross site scripting and other...
-
/intruder-alternatives
Intruder is a security monitoring platform for internet-facing systems.
-
/rapid7-metasploit-alternatives
Penetration testing solution for risk validation.
-
/skybox-vulnerability-control-alternatives
Skybox Vulnerability Control is an industry-leading cyber-security management solution that allows threat-centric vulnerability prioritization and scan-less vulnerability assessments in order to address security challenges within large and complicat…
-
/invicti-formerly-netsparker-alternatives
Netsparker Security Scanner is a simple-yet-powerful web-based security scanner that automatically identifies XSS, SQL Injection, and all the other vulnerabilities and security flaws in sites, web apps, and web services.
-
/httpcs-security-alternatives
Cyber security solution for protecting websites and web apps
-
/code42-alternatives
Code42 is a SaaS solution for enterprises that secures all user data on one secure platform, leaving you and your business secure in the knowledge that both your employee's and customer's data is protected. Read more about Code42.
-
/shodan-alternatives
Shodan is the world's first search engine for Internet-connected devices.
-
/fiddler-alternatives
Fiddler is a debugging program for websites.
-
/rapid7-nexpose-alternatives
Network vulnerability and risk management solution.
-
/openvas-alternatives
The Open Vulnerability Assessment System (OpenVAS) is a framework of several services and tools...