CloudEye AWS Security
Security, compliance & cost for AWS & Azure cloud services
CloudEye AWS Security Alternatives
The best CloudEye AWS Security alternatives based on verified products, community votes, reviews and other factors.
Latest update:
-
Wallarm WAF is AI-powered Platform that automates real-time application protection combines Active Threat Verification engine with a DevOps friendly NG-WAF and security testing for websites, microservices and APIs across public and private clouds.
-
Jscrambler is a JavaScript protection solution that makes apps self-defensive, resilient against tampering, malware injection, & code theft.
-
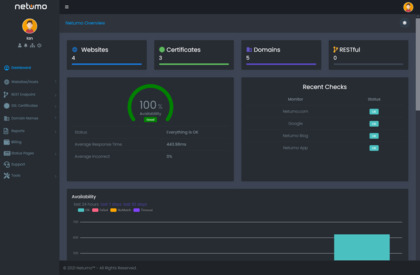
Ensure healthy website performance, uptime, and free from vulnerabilities. Automatic checks for SSL Certificates, domains and monitor issues with your websites all from one console and get instant notifications on any issues.
-
IMMUNIO is a runtime application self-protection (RASP) solution, providing comprehensive web application security for multiple frameworks.
-
Auth0 is a program for people to get authentication and authorization services for their own business use.
-
Tor is free software for enabling anonymous communication.
-
Free Website Uptime Monitoring
-
CrashPlan for Small Business backup software offers the best way to back up and store business & enterprise data securely - offsite, onsite & online in the Cloud.
-
Secure Content Delivery Network, DDoS, WAF Service
-
Cloudflare is a global network designed to make everything you connect to the Internet secure, private, fast, and reliable.
-
Flexera Software Vulnerability Manager provides solutions to continuously track, identify and remediate vulnerable applications.
-
Avast security software products are developed for Microsoft Windows, Mac OS X, Android and Linux users by AVAST Software.
-
Track, record, alert and visualize performance and availability of IT resources
-
Pulse Secure provides a consolidated offering for access control, SSL VPN, and mobile device security. Contact Pulse Secure at 408-372-9600 to get a free demo.